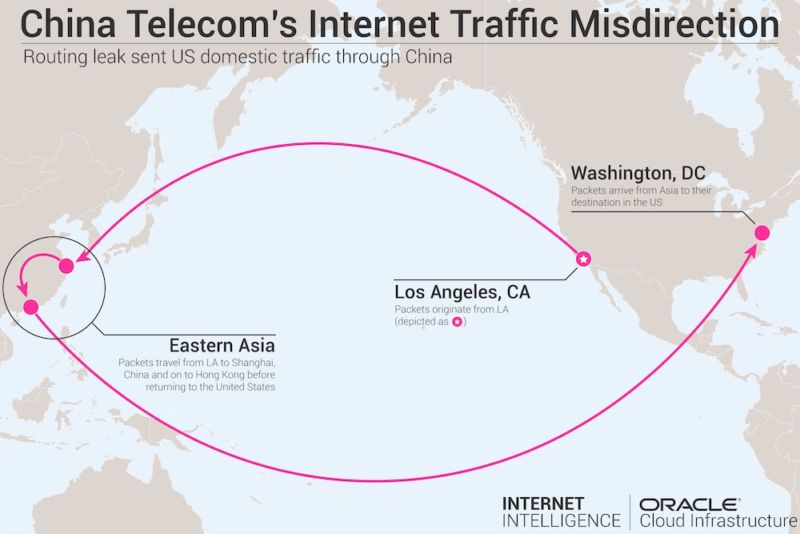
A research paper published by researchers from the US Naval War College and Tel Aviv University states that a Chinese state-owned telecommunications company has been “hijacking the vital internet backbone of western countries.”
Needles to say, the paper has been causing a lot of friction online: the researchers accuse China Telecom of hijacking and detouring internet traffic via its internet infrastructure.
Even so, for a while it was still unclear if the paths were actual hijackings or if they had been caused just by some sort of glitch but today, Doug Madory, Director of Oracle’s Internet Analysis division has officially confirmed that China Telecom has been somehow engaged in the internet traffic misdirection.
“I don’t intend to address the paper’s claims around the motivations of these actions. However, there is truth to the assertion that China Telecom (whether intentionally or not) has misdirected internet traffic (including out of the United States) in recent years. I know because I expended a great deal of effort to stop it in 2017.”
Back in 2017, traffic that originated in Los Angeles first went through a China Telecom facility located in Hangzhou, China, before eventually reaching its destination in Washington DC.
According to Madory, a larger misdirection that started in 2015 was due to an autonomous system that belongs to China Telecom: the AS4134. This system handled the routing announcements of AS703, Verizon’s Asia Pacific AS, incorrectly. This caused a number of international carriers such as Telia’s AS1299, Tata’s AS6453, GTT’s AS3257, and Vodafone’s AS1273, to send their data through China Telecom instead of the usual multinational telecoms, data which was intended for the Verizon Asia Pacific.
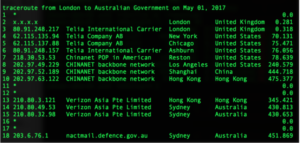
Traceroute that shows the path of internet traffic coming in from London intended to address space that belongs to the Australian government. Before the routing issue, it never crossed paths with China Telecom
Since then, most of the traffic that passed through Verizon’s AS703 was rerouted through the Chinese AS4134.
These hijacks can have disastrous consequences: earlier this year, someone used this method to redirect Amazon Route 53 domain-resolution traffic. The event lasted for two hours and allowed the anonymous attackers to steal around $150,000 in digital coins by routing people to a fake MyEtherWallet.com website.
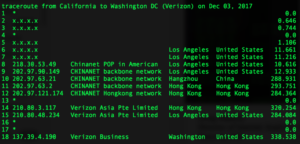
Traceroute from within the U.S intended for Verizon U.S. The path the traceroute took outside of the country is clear.
Routing traffic through networks that are controlled by attackers allows them to monitor, corrupt and even completely modify any data that lands in their lap uncrypted but even uncrypted data can find its match, with the right tools.
Madory’s recently published paper endorses an RPKI-based AS path verification, which is supposed to be a mechanism that, if deployed, can stop such events from happening.
Follow TechTheLead on Google News to get the news first.