Is this the biggest cybersecurity sting in history? The FBI, AFP (Australia’s Federal Police), Europol and multiple agencies took over an encrypted chat app called ANoM.
They then spread it to criminals, let them talk, and finally arrested them en-masse.
Authorities watched criminal communications closely since 2018, then arrested more than 800 individuals in little under 3 days, seizing tens of millions in assets and metric tons of drugs in multiple countries.
If you look at how the sting worked, you’ll no doubt be impressed at the sheer scale and cleverness of it.
The ANoM app was a black-market product “only accessible on specially prepared mobile phones”, according to CNN, which promised criminals secure, encrypted communications.
ANoM was only available on phones that had been stripped of the ability to make calls or send emails. A phone with ANoM on it could send messages only to another ANoM-using phone, which could only be obtained from a criminal – or, in this case, the FBI.
Considering the promise of secure, secret communications, ANoM phones spread like wildfire through the criminal underground.
The FBI distributed 12,000 phones with the ANoM app to more than 300 criminal syndicates in more than 100 countries.
“The devices organically circulated and grew in popularity among criminals, who were confident of the legitimacy of the app because high-profile organized crime figures vouched for its integrity,” the AFP said in a statement.
So, what went wrong?
The AnOM was actually in the hands of the FBI ever since 2018, when its original developer surrendered it to agents in order to get a short sentence. That means that those ‘encrypted communications’ were actually spied on by multiple agencies, from the FBI to AFP and Europol.
Here’s one ANoM screenshot showing exactly what the chat app was used for.
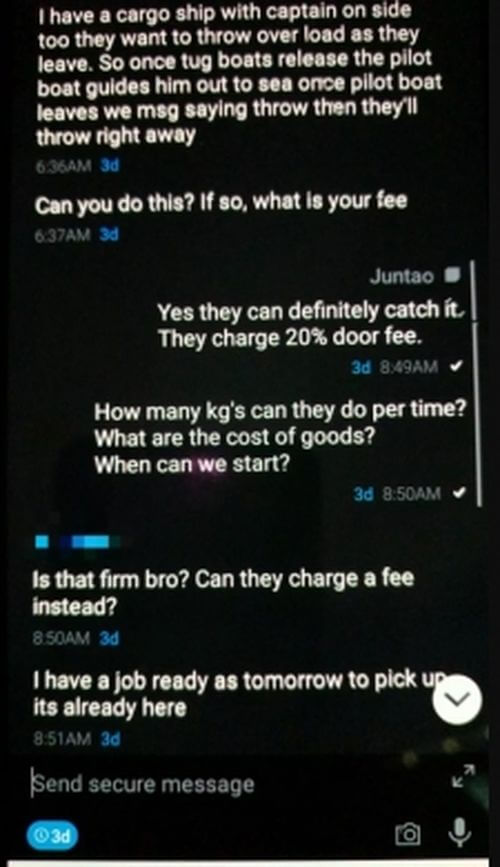
“The FBI’s review of ANOM users’ communications worked like a blind carbon copy function in an email. A copy of every message being sent from each device was sent to a server in a third-party country where the messages were collected and stored,” explained a press release from US Attorney’s Office, Southern District California.
The same press release outlined just how innovative and effective this approach is.
“Hardened encrypted devices usually provide an impenetrable shield against law enforcement surveillance and detection. The supreme irony here is that the very devices that these criminals were using to hide from law enforcement were actually beacons for law enforcement. We aim to shatter any confidence in the hardened encrypted device industry with our indictment and announcement that this platform was run by the FBI,” said Acting US Attorney Randy Grossman.
The FBI worked together with the AFP to bust the criminal network coordinating through that app and the results are nothing short of amazing.
“3.7 tonnes of drugs, 104 weapons, $44,934,457 million in cash, and assets expected to run into the millions of dollars, have been seized under Operation Ironside since 2018.
The AFP also acted on 20 threats to kill, potentially saving the lives of a significant number of innocent bystanders, with intelligence referred to state police agencies which took immediate action.
More arrests are expected domestically and offshore under a coordinated global response connected to Operation Ironside.
The AFP is also likely to seek extradition requests of a number of persons of interest living overseas. It comes as there have been tonnes of drugs and hundreds of arrests overseas,” outlined AFP about their results in Australia.
In the States, the results of this operation, called Trojan Shield, are even more awe-inspiring.
In the past 48 hours, 9000 officers were deployed worldwide in about 700 locations, making 800 arrests.
They seized more than 32 tons of drugs, $48 million in various currencies and 250 firearms. They also dismantled more than 50 clandestine drug labs.
Follow TechTheLead on Google News to get the news first.