Search results for "security"
-

 4.2KPhones
4.2KPhonesApple Accused of Helping Chinese Authorities Stifle Protests By Secretly Tweaking Airdrop
Apple is under fire from security experts and civil rights advocates for its handling of iPhone features in China. Apple is accused...
-

 2.7KGuides
2.7KGuides4 Contemporary Examples of Design Thinking In Action
Have you ever wondered just what goes into designing the computer applications you use on a daily basis? When it comes to...
-

 3.8K1Security
3.8K1SecurityHow You Can Protect Your Identity While Streaming? How to Keep Your Identity Secure
Online streaming is getting more and more popular but the dangers are increasing as well. Streaming makes your online identity vulnerable to...
-
 4.0KSecurity
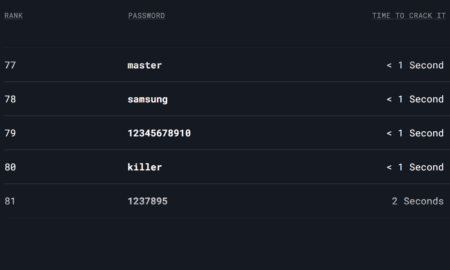
4.0KSecurityPeople, Stop Using “Samsung” As the Password For Your Phone
It’s no secret that hackers can most passwords in seconds but this new report shows they don’t even have to try, since...
-
 3.1KSmart Life
3.1KSmart LifeImpact of IoT on Enhancing the Customer Experience
We go about our lives with technology as a vital part of it and who knows how long that’s been going on....
-

 3.3KGuides
3.3KGuidesHow to Open MBOX Files in Chrome
How to Open MBOX Files in Chrome? Nowadays, the MBOX to HTML conversion demand has increased exponentially. The key reason is that...
-

 2.4KSecurity
2.4KSecurityWhy Invest in Identity Theft Protection Today
The moment you share any details online, you become susceptible to cyberattacks. Statistics indicate that 4.5 percent of U.S. residents experience identity...
-
 6.3KGaming
6.3KGaming6 Reasons Why You Should Always Use A VPN When Streaming
If you’ve spent any amount of time on the internet, chances are you would have come across the term “VPN.” If you...
-

 3.3KFuture
3.3KFutureNew EU Rules Plan to Make It Easier For Individuals to Sue Manufacturers for Smart Home Devices that Don’t Work Properly
On Wednesday, the European Commission proposed a new set of rules under the “AI Liability Directive”. If adopted, they will make it...
-

 7.1KPhones
7.1KPhonesIQOO 9T Review: The Vivo Flagship You Wish You Could Buy
My colleague was super impressed by the Vivo X80 Pro and thought it could be 2022’s flagship killer but I’d like to...
-

 4.1KSecurity
4.1KSecurityPSA: Hackers Are Now Embedding Malware In James Webb Telescope Image
You have to give credit where credit is due: hackers are infinitely creative! A security researcher warns of a new malware campaign...
-

 4.7KSecurity
4.7KSecurityA 14-Year-Old Cracked The Codes on Australia’s New Coin In Just Over An Hour
Australia’s new limited edition commemorative coin was launched with five different encryption codes on it but it took little over an hour...
-

 11.5KFuture
11.5KFutureWhat Deepfakes Can Do: The Best Videos And the Deepfake Apps Changing Reality
For the last four years, deepfake videos have challenged reality, turning empirical evidence into an artifact of the past. Can you really...
-

 2.9KPhones
2.9KPhonesAutomated Mobile Testing – How Does It Work?
Automated mobile testing ensures your apps work as they should without any performance, security, or other bug issues. Mobile business applications must...
-

 4.5KPhones
4.5KPhonesAre You A Clumsy Phone User? These Six Things Are Must-Haves
Phones are probably the most important tool in this day and age – but what to do if you’re a clumsy phone...








